
The essence of information security
In this article I provide a general outline for understanding computer security (simple, but far from obvious!) It will be very useful as a reference for future episodes on the topic.
We live in the information age: information and in particular its security therefore plays a key role in all our activities.
But what is security?
Security is in general a risk analysis and management problem, where risk arises from the violation of desired requirements for a given system. Without a precise definition of the system and its desired requirements, it is therefore impossible to define what security is.
So what is information security?
It is a security problem applied to information. When information is (mainly) managed by automated systems (computers), it is called computer or cyber-security. In this case, security requirements must be applied to the same systems that manage information (computers and hardware devices), as well as to executable code (software programs).
In order to start talking about information security, it is therefore necessary to define:
- what information needs to be protected: think about the key objectives of your business;
- requirements for the information to be protected; we can identify common ones, which must always be contemplated, at various levels of abstraction.
Three fundamental requirements
In general, it is desirable that information is:
- Accessible to authorized entities only (Confidentiality)
- Modifiable by authorized entities only (Integrity)
- Accessible and/or modifiable within a certain time frame by the authorized entities (Availability)
An entity can be any system, including -and most importantly- people.
Two functional requirements
The fundamental security requirements mentioned above are inextricably linked to the concept of authorization which can be broken down into two functions:
- Authentication: Identification of the entity that wants to access the information;
- Access control: Definition and limitation of the operations that an entity can carry out.
These mechanisms can be defined as functional requirements for achieving the previous fundamental requirements.
Risk analysis and treatment
In general, nothing is certain. In this specific case, it is not possible to state with absolute certainty that any of the defined security requirements are actually satisfied. There is always a risk (effect of uncertainty on objectives) associated to a violation of security requirements.
Information security can therefore be evaluated only in terms of:
- ANALYSIS: identification of risks linked to the violation of security requirements; it is necessary to evaluate the probability and impact of unexpected events on the key objectives of your business; in the operational phase it requires event monitoring to identify violations or potential violations (vulnerabilities) of the requirements.
- TREATMENT: execution of actions aimed at reducing the risk of violations to an acceptable level (mitigation). Generally, since any activity carry a risk, to completely eliminate a risk we may choose not to carry out the activity that causes it.
These two phases can be considered as process requirements, since they must be part of a continuous process integrated into all systems that manage information. These steps are actually the pillars of all major standards and guidelines on the subject:
- International ISO 31000 (2018) , ISO/IEC 31010 (2019) , ISO/IEC 27005 (2018) , ENISA Cloud Computing Risk Assessment (2009) , ENISA Risk Management/Risk Assessment (RM/RA)
- National (some relevant examples) US NIST SP800–30r1 , NIST SP800–37r2 , IT Agid — Guideline for the development of secure software , IT National Framework for Cybersecurity and Data Protection , FR CNIL Privacy Impact Assessment — Methodology (2018)
General scheme for information security
At this point we are ready to present a general framework for information security, based on requirements at three levels of abstraction: fundamental, functional and process level. This scheme will be fundamental to frame and find a solution to any security problem that we are going to analyse!
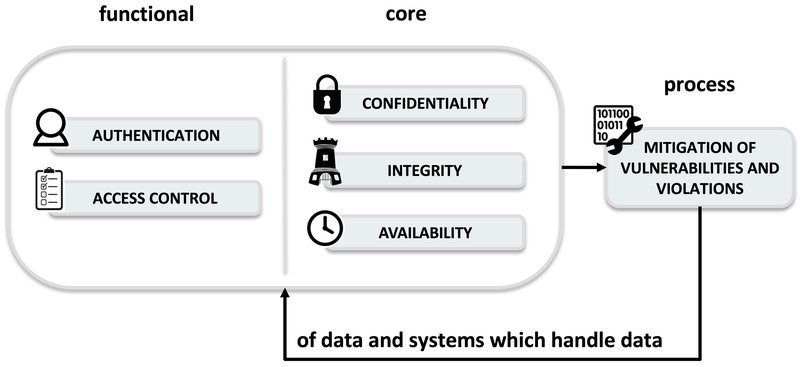
I use this (simple) framework in practically all my cybersecurity courses — I also used it in a presentation at the OWASP Day held in Cagliari (Sardinia, Italy) in 2018 to highlight the limitations of the OWASP TOP 10 (ranking of the 10 most popular risks for systems on the web). OWASP (Open Web Application Security Project) is the most important open-source project for web security.
Find more blog posts with similar tags
